Chrysalide is a brand-new reverse engineering tool. Its early features allow it to be used to succeed in small online challenges.
This presentation provides some details about its advantages compared to other similar tools, based on a past CTF.
Foreword
The current presentation is based on a WriteUp from Mathy Vanhoef:
The aim of this page is not to write again such a complete report, but to focus on some particular points, where Chrysalide can offer some original answers.
Thus, the setup of a VM will not be explained once again here. Moreover, the readers who wish to learn the way to a successful exploitation will need to refer to the original article.
Highlight 0: where to begin?
The GNU tool « objdump » (v 2.22) is completely lost with the ARM and Thumb-2 encoding mixes. Thus the entry point is not well disassembled with it.
The GNU debugger can be used with some tricks:
$ readelf -h ./trafman | grep Entry
Entry point address: 0x880d
$ gdb ./trafman -batch -ex "disass 0x880d"
No function contains specified address.
$ gdb ./trafman -batch -ex "x /16i 0x880d"
0x880d: mov.w r11, #0
0x8811: mov.w lr, #0
0x8815: pop {r1}
0x8817: mov r2, sp
0x8819: push {r2}
0x881b: push {r0}
0x881d: ldr.w r12, [pc, #16] ; 0x8830
0x8821: str.w r12, [sp, #-4]!
0x8825: ldr r0, [pc, #12] ; (0x8834)
0x8827: ldr r3, [pc, #16] ; (0x8838)
0x8829: blx 0x872c <__libc_start_main>
0x882d: blx 0x87c8 <abort>
0x8831: ldrh r5, [r5, #46] ; 0x2e
0x8833: movs r0, r0
0x8835: strh r1, [r4, #62] ; 0x3e
0x8837: movs r0, r0
The version number is not provided, but Mathy Vanhoef shows in his report that problems remain with IDA:
Chrysalide automatically recognizes the encoding modes of instructions located at the entry point. There is no need to proceed to any extra manual operations in order to convert and to discover the run code.
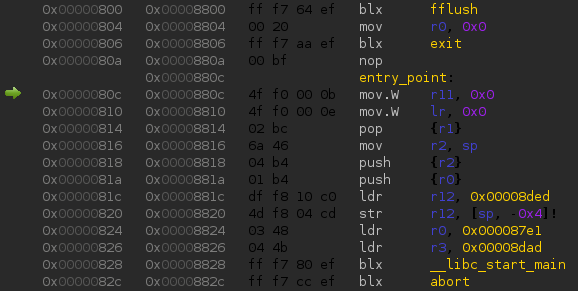
The entry point is visualized by a small green arrow on the left of addresses.
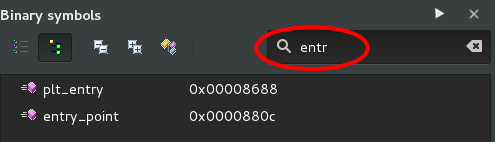
At any time, the fastest and simplest way to reach this entry point again is to use the symbols list, by default on the right side, then to search « entry_point » there ; the symbol selection moves the current view at the location of this symbol.
It is also possible to switch on graphic mode, where the code is cut into basic blocks, by pressing the « F3 » key.
Highlight 1: retrieve a valid username.
A valid username is required to start the game.
In order to locate the code responsible for checks, we only have to provide a random username. For instance « test ». Without a stroke of luck, the program displays the following message:
$ ./trafman
_______ __ __ __
|__ __| / _| \/ |
| |_ __ __ _| |_| \ / | __ _ _ __
| | '__/ _` | _| |\/| |/ _` | '_ \
| | | | (_| | | | | | | (_| | | | |
|_|_| \__,_|_| |_| |_|\__,_|_| |_|
Welcome to the Traffic Lights Management of SmartCity. Please authorize.
Username: test
ERR Invalid User.
In the strings panel, we write « ERR Invalid » as filter. The strings list gets then reduced, and the details of the error message quickly appear.
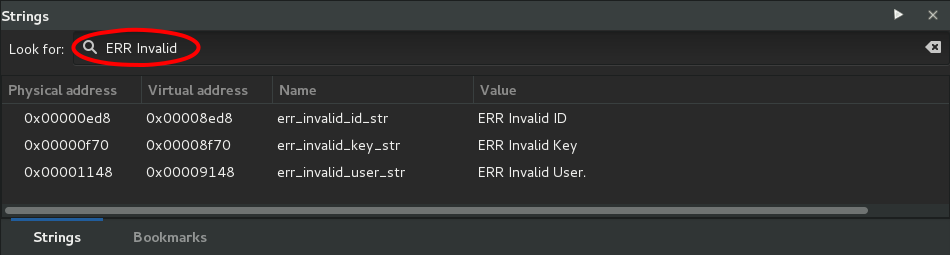
A right click on the string pops up a contextual menu. We then look for references in order to find all the places handling the message.
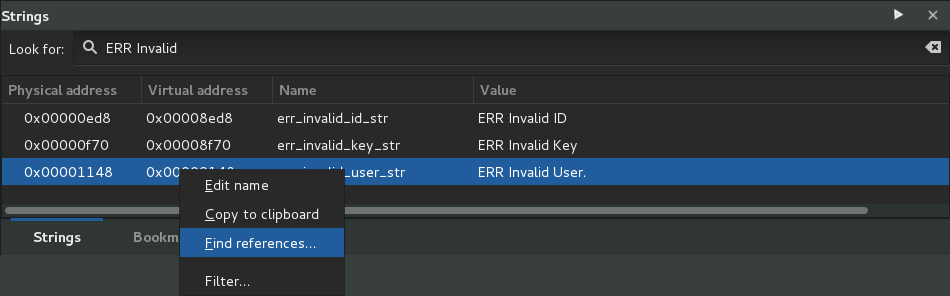
The string is used in several places. Two of them are located in a function defined at the address 0x8cbc. We choose to look at the first proposed reference.
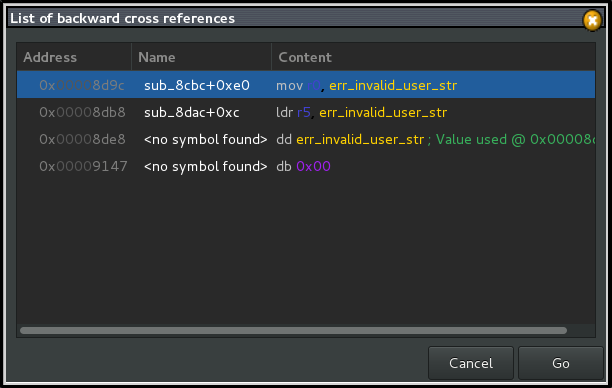
In the code, the call to the function « strncmp » compares something (most likely the value provided by the user) and an ASCII string renamed « traffic_operator_str » by Chrysalide.
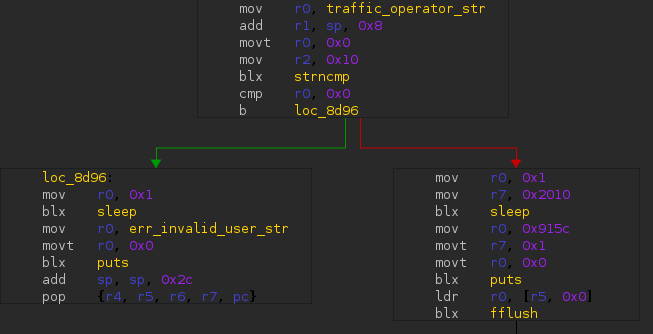
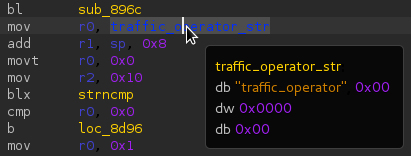
The real value of this field can be revealed in two ways:
- either by following references: the caret has to get moved on the word « traffic_operator_str » and a key press on « Enter » drives to the target (shortcut for the menus « Edition » / « Follow the reference »).
- either by leaving the mouse pointer over the word « traffic_operator_str ». THe target content appears in a new tooltip.
Highlight 2: defeating ASLR and NX with ROP.
Chrysalide offers its own method to look for ROP gadgets. Its main advantages are:
- the extension is fast, because it is written in C and minimalist in terms of analysis features.
- its behavior is strongly generic: the return properties are defined at the disassembling time, not during the search process.
Except from characteristics specific to a given architecture (like the two complementary modes ARM and Thumb here), the search extension can get used to any machine code.
We launch the plugin using the « Plugins » menu, then « List all ROP gadgets ».
It is then up to the user to choose between two options: either to study an already loaded binary from the current project, or to load a new binary.
We choose here the second option, and we provide the pathname to the libc:
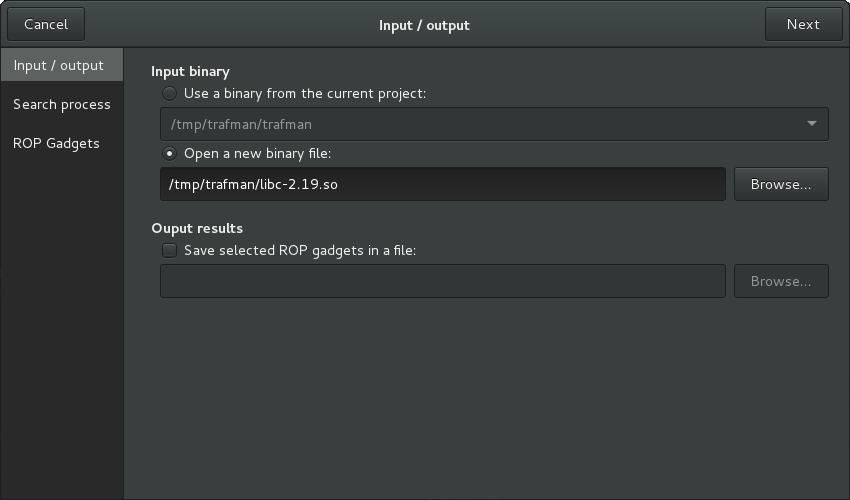
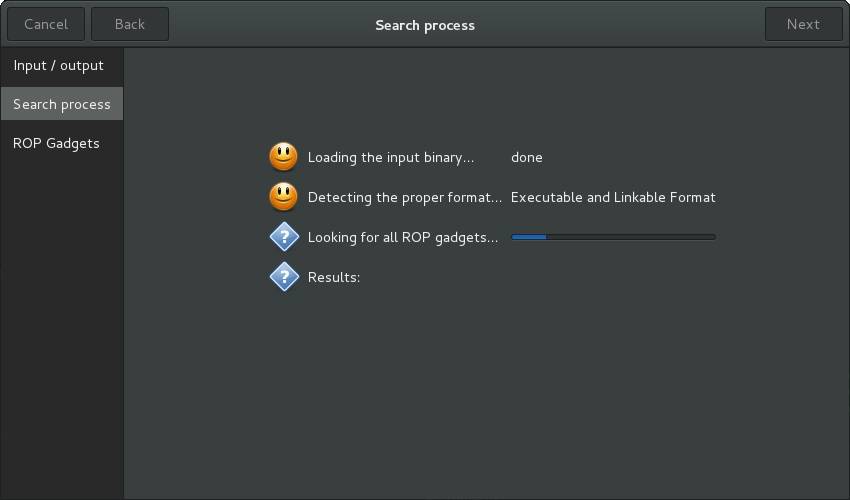
The search process takes several seconds ; one can track the progress of the analysis:
All the results are listed on the last page of the dialog box. It is possible to switch from an encoding to another one (ARM/Thumb) or to filter the gadgets against regular expressions.
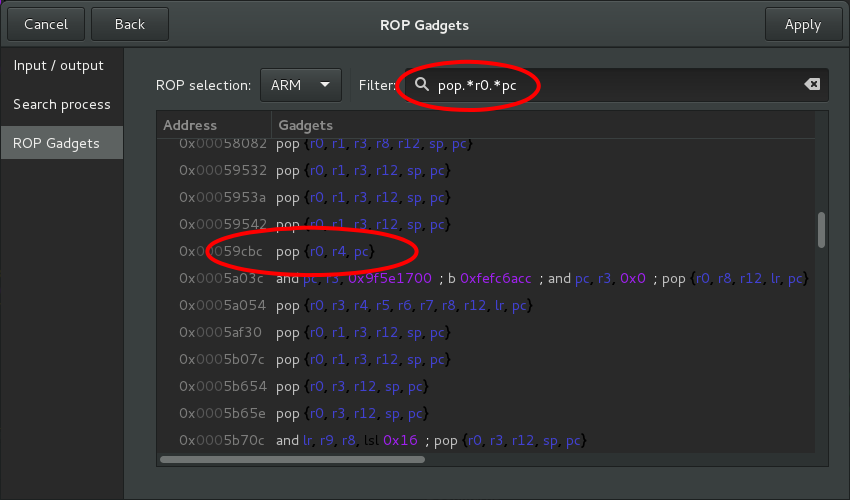
We finally find the expected results, the same than those obtained with the Shell commands:
arm-linux-objdump -d libc.so.6 | grep "pop.*r0.*pc"
Conclusion.
Chrysalide offers interesting features and a GUI to deal with ARM ELF binaries.
It works well in some limited cases for now, so the roadmap is to stress it again and again to improve the code.
As some new features are scheduled for the next months, there will probably be other blog posts soon.
Posted on May 13, 2015 at 01:18.
